Keeping you informed of the changing landscape of information and cyber security within the governance, risk and compliance space!
As cybersecurity threats and regulatory requirements continue to evolve in Australia, organisations are under increasing pressure to not only safeguard their information and technology assets but also provide assurance they are doing so.
Governance, Risk, and Compliance (GRC) can, when properly implemented, provide the means to meet these demands - ensuring accountability, legal compliance, effective security risk management and assurance to stakeholders.
In this article we explore the core elements of GRC, outline new legislative developments, and highlight changes shaping the Government sector in the Australian cybersecurity landscape.
What Exactly is GRC?
Security principles (CIA)
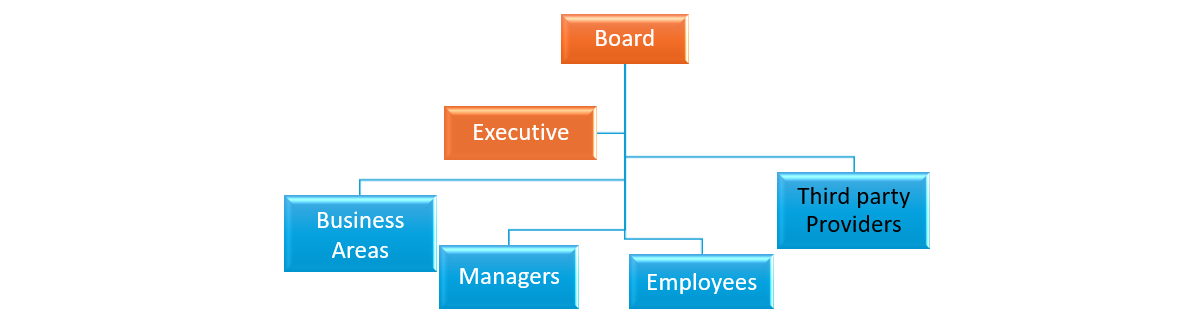
Governance
It is crucial for Boards and the Executive to exercise authority and implement governance; ensuring information and cyber security is endorsed, owned, sponsored and everyone is made aware of their accountabilities and responsibilities.
Information and cyber security policies should be created and aligned with overarching frameworks and policies.
Critical information and technology assets need to be identified, valued, and resources applied to protect them from security threats and risk.
Risk
Traditional frameworks may not be designed to capture security risks, so organisations must ensure they can identify, assess, mitigate and treat cyber security threats. This approach enables the ongoing protection of assets based on criticality, risk impact and consequence.
Compliance
Adherence to relevant security and privacy legislation and regulations is of paramount importance. Organisations must select appropriate security controls to be able to capture, implement, maintain, manage and measure their compliance obligations.
Procurement and Contract Management
Procurement and contract management of third parties providing information and/or technology based services is also an area that organisations grapple with. Third parties have been used as attack vectors into organisations as highlighted in cyber security incident investigations.
Accountability cannot be outsourced…
Organisations may require assistance with due diligence through to the identification of security controls in the form of clauses in contractual agreements. Those security clauses are based on the results of a security threat and risk assessment which can be performed onsite or offsite depending upon the services to be provided by the third party.
The Ever-evolving information and cyber security environment
The information and cyber security landscape in Australia is rapidly evolving with changes to legislation and regulation governing how organisations manage their privacy obligations, security threats and risks. This is due to the extent and impact in terms of consequence, that were realised in the aftermath of major cyber security breaches here in Australia and overseas over the last few years.
New technologies such as AI bring new challenges to organisations in regard to maintaining privacy and security over their information and technology assets.
The cyberattack surface in terms of target selection is also changing as cyber criminals look for lucrative targets, i.e., high-end retail shops because they are perceived to be soft targets. In terms of foreign government backed entities, sectors considered to be critical infrastructure are still being targeted.
So, what has changed?
Australian Government
Security of Critical Infrastructure and Other Legislation Amendment (Enhanced Response and Prevention) Act 2024 (ERP Act)
Data storage systems
Managing consequences of incidents
Protected information
Direction to vary risk management program
Telecommunications Security
Cyber Security Act 2024
Security standards for smart devices
Obligations to report ransomware
Information Security Manual (ISM)
ISM version March 2025 contains new and revised controls. A snapshot of the changes includes:
Guidelines for cybersecurity roles - new section which contains security controls for Boards and the Executive for embedding cybersecurity within their organisations
Guidelines for cybersecurity documentation - new security control for the development of a change and configuration management plan
Amendments and new controls relating to Microsoft Active Directory Domain Services account hardening etc.
Australian Cyber Security Centre (ACSC)
The ACSC has released a variety of new documents. A snapshot of recently published documents:
Implementing SIEM and SOAR platforms
AI Data Security
GEO-blocking in context: Realities, risks and recommendations
Preparing for and responding to denial-of-service attacks
Foundations for modern defensible architecture
Protective Security Policy Framework (PSPF)
PSPF now comes under the Dept of Home Affairs. The PSPF has been fully revised and is now incorporated into one document instead of 16 distinct policies. Specific security controls are now numbered similar to those in the ISM.
The Dept of Home Affairs issued six directives, Shown here in year order:
Direction 001-2023 on the TikTok application
Direction 001-2024 Managing Foreign Ownership, Control or Influence Risks in Technology Assets
Direction 002-2024 Technology Asset Stocktake
Direction 003-2024 Supporting Visibility of the Cyber Threat
Direction 002-2025 on Kaspersky Lab, Inc. Products and Web Services
Direction 001-2025 on DeepSeek Products, Applications and Web Services
Office of the Australian Information Commissioner (OAIC)
“25% year-on-year increase in data breach notifications”
New statistics for July to December 2024, show the OAIC was notified of 595 data breaches, ending the year with a total 1,113 notifications. This is a 25% increase from 893 notifications in 2023.
Top 5 sectors to notify data breaches
Victorian Government
There have been a raft of changes in overall responsibility functions for cyber security within the Government.
Victorian Auditor-General’s Office (VAGO)
“90% of Victorian Government agencies experienced a cybersecurity incident”
VAGO intend to audit Cybersecurity Infrastructure in 2025/2026 and plan to examine the effectiveness of agencies’ asset management in relation to the cloud environment and the effectiveness of controls associated with cloud-based infrastructure.
Such an audit will examine the contractual agreements agencies have with third party cloud providers, the designated technical security controls embedded in the cloud-based infrastructure to protect public sector information assets and the overall governance, risk and compliance frameworks in place, including cyber incident response.
Dept of Government Services (DGS)
DGS leads the State’s cyber security incident arrangements. They report that 9 out of 10 Victorian Government organisations experienced a cyber incident in 2024.
DGS have revised and have taken ownership of the Cyber Security Incident Management Plan for limited, major and critical cyber security incidents across the Victorian Government sector. The Victorian Cyber Information Security Officer is situated in DGS.
Emergency Management Victoria (EMV)
EMV have developed the State Emergency Management Plan – Cyber Security Sub-plan for cyber emergencies.
Thanks for Reading, More To Come!
We are noticing a flow-on effect of the cybersecurity requirements to other sectors that come under the auspices of Australian and State Government legislation and regulations, i.e., Not-for-Profits, Aged Care, Health Services etc.
Bookmark the IPSec blog to stay in touch with developing cyber security information and news, including follow-up articles discussing information and cyber security compliance requirements in other sectors.
Need help with GRC?